薛佳宇,使用Restful查看/新增/删除V7防火墙安全策略配置
组网及说明
测试防火墙环境:
F1000-AI-60 Version 7.1.064, Release 8660P33
客户端环境:
Postman for Windows Version 9.31.27
配置步骤
一、防火墙开启Restful,并配置用于登陆防火墙的用户
Sys
ip https enable
restful https enable
#
local-user xxxx
password simple xxxx
service-type https
authorization-attribute user-role network-admin
#
二、登陆防火墙
#方法使用POST,URL为:https://10.88.142.143/api/v1/tokens ip为防火墙地址
#选择Authorization,type更改为Basic Auth,右侧输入一个可以使用https方式登陆防火墙的账号及密码,最后点send
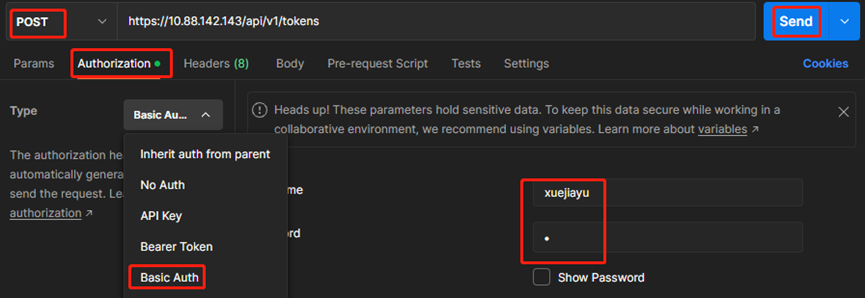
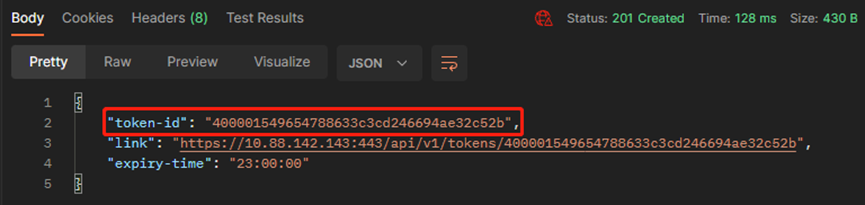
#记录返回的token-id,后续会使用这个字符串作为验证的凭据
三、查看安全策略配置
1、查看测试设备当前的安全策略规则配置
#
security-policy ip
rule 0 name trust2untrust
action pass
logging enable
counting enable
source-zone Trust
destination-zone Untrust
source-ip-subnet 172.16.10.0 255.255.255.0
rule 1 name untrust2trust
action pass
counting enable
source-zone Untrust
destination-zone Trust
destination-ip-host 172.16.10.100
service https
rule 2 name local2untrust
action pass
source-zone Local
#
2、查看Restful API手册,可以看到读取安全策略rule规则的API为
GET /api/v1/SecurityPolicies/GetRules
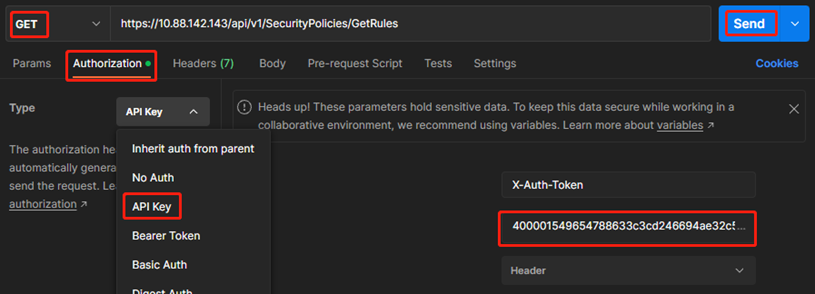
3、创建一个GET请求,完成读取操作
#新建GET请求,填入上述URL
#Authorization选择API key,红框处填入“一、登陆防火墙”中获取到的token-id,最后点击send
#得到如下输出
{
"GetRules": [
{
"Type": 1,
"ID": 0,
"Name": "trust2untrust",
"Action": 2,
"SrcZoneList": {
"SrcZoneItem": [
"Trust"
]
},
"DestZoneList": {
"DestZoneItem": [
"Untrust"
]
},
"SrcSimpleAddrList": {
"SrcSimpleAddrItem": [
"172.16.10.0/24"
]
},
"Enable": true,
"Log": true,
"Counting": true,
"CountingPeriod": 0,
"CountingTTL": 0,
"Count": 0,
"Byte": 0,
"SessAgingTimeSw": false,
"SessPersistAgingTimeSw": false,
"AllRulesCount": 3,
"Valid": true,
"ValidStatus": 5
},
{
"Type": 1,
"ID": 1,
"Name": "untrust2trust",
"Action": 2,
"SrcZoneList": {
"SrcZoneItem": [
"Untrust"
]
},
"DestZoneList": {
"DestZoneItem": [
"Trust"
]
},
"ServGrpList": {
"ServGrpItem": [
"https"
]
},
"DestSimpleAddrList": {
"DestSimpleAddrItem": [
"172.16.10.100"
]
},
"Enable": true,
"Log": false,
"Counting": true,
"CountingPeriod": 0,
"CountingTTL": 0,
"Count": 0,
"Byte": 0,
"SessAgingTimeSw": false,
"SessPersistAgingTimeSw": false,
"AllRulesCount": 3,
"Valid": true,
"ValidStatus": 5
},
{
"Type": 1,
"ID": 2,
"Name": "local2untrust",
"Action": 2,
"SrcZoneList": {
"SrcZoneItem": [
"Local"
]
},
"Enable": true,
"Log": false,
"Counting": false,
"CountingPeriod": 0,
"CountingTTL": 0,
"SessAgingTimeSw": false,
"SessPersistAgingTimeSw": false,
"AllRulesCount": 3,
"Valid": true,
"ValidStatus": 5
}
]
}
四、添加安全策略规则
1、假设要新增一个规则:名称为t2u,源安全域trust,目的安全域为untrust和local,源ip地址为172.16.10.1/32和172.16.20.0/24,动作为允许。步骤为:
(1)新建一个ipv4rule规则,动作为允许
#查找API手册可知,API为POST /api/v1/SecurityPolicies/IPv4Rules
#新建POST请求,填入上述URL
#Authorization选择API key,红框处填入“一、登陆防火墙”中获取到的token-id
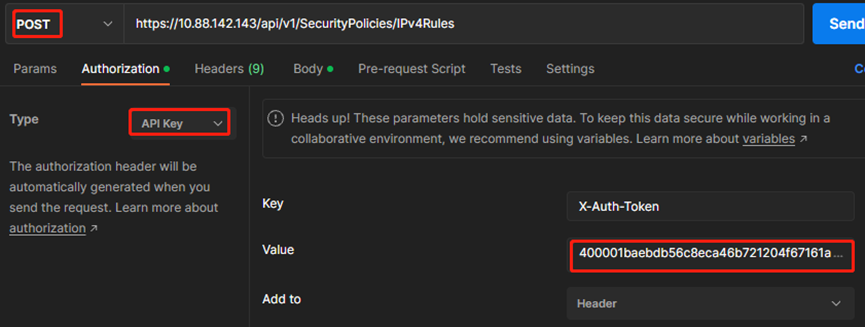
#Body选择raw—JSON,输入
{
"ID": 100,
"RuleName": "t2ut",
"Action": 2
}
#确认返回值为201
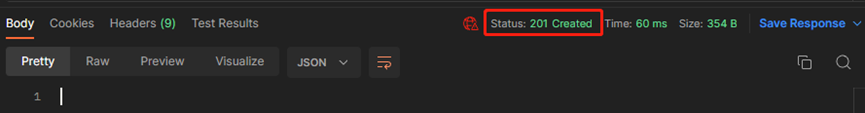
(2)为新增的rule添加源安全域
#查找API手册可知,API为POST /api/v1/SecurityPolicies/IPv4SrcSecZone
#新建POST请求,填入上述URL
#Authorization选择API key,红框处填入“一、登陆防火墙”中获取到的token-id
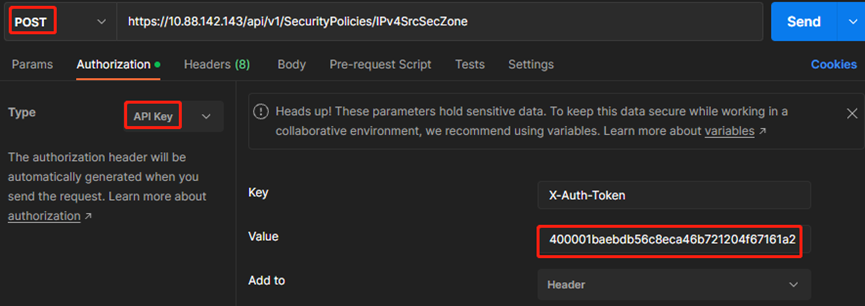
#Body选择raw—JSON,输入
{
"ID": 100,
"SeqNum": 10,
"IsIncrement": false,
"NameList":
{"NameItem":
[
"trust"
]
}
}
#确认返回值为201
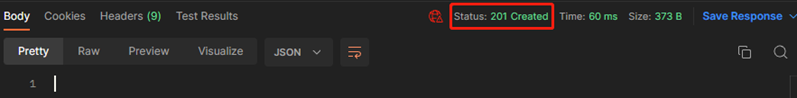
(3)为新增的rule添加目的安全域
#查找API手册可知,API为POST /api/v1/SecurityPolicies/IPv4DestSecZone
#新建POST请求,填入上述URL
#Authorization选择API key,红框处填入“一、登陆防火墙”中获取到的token-id
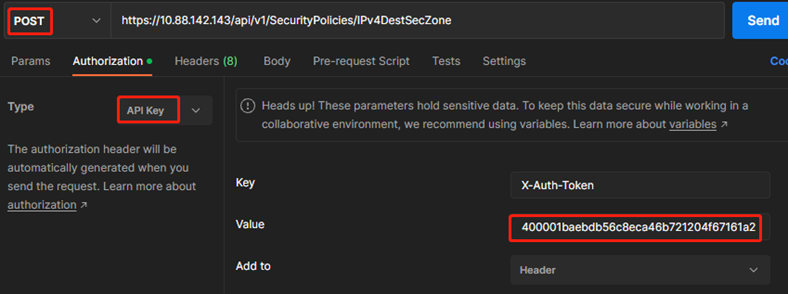
#Body选择raw—JSON,输入
{
"ID": 100,
"SeqNum": 10,
"IsIncrement": false,
"NameList":
{"NameItem":
[
"untrust",
"local"
]
}
}
#确认返回值为201
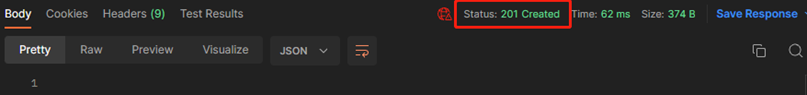
(4)为新增的rule添加ipv4源地址
#查找API手册可知,API为POST /api/v1/SecurityPolicies/IPv4DestSimpleAddr
#新建POST请求,填入上述URL
#Authorization选择API key,红框处填入“一、登陆防火墙”中获取到的token-id
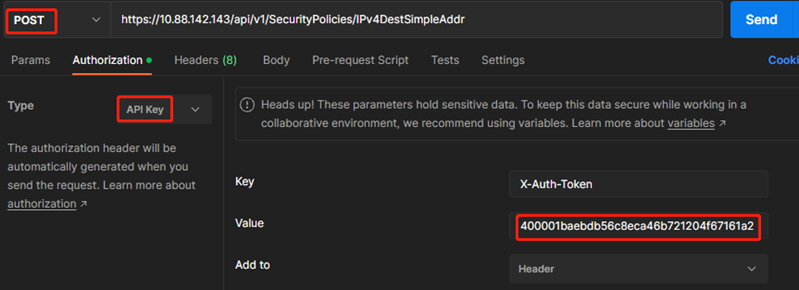
#Body选择raw—JSON,输入
{
"ID": 100,
"SeqNum": 10,
"IsIncrement": false,
"SimpleAddrList":
{"SimpleAddrItem":
[
"172.16.10.1",
"172.16.20.1/24"
]
}
}
#确认返回值为201
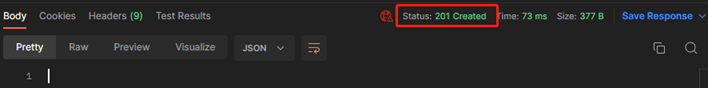
2、查看命令行配置,确认下发成功
#
security-policy ip
rule 0 name trust2untrust
action pass
logging enable
counting enable
source-zone Trust
destination-zone Untrust
source-ip-subnet 172.16.10.0 255.255.255.0
rule 1 name untrust2trust
action pass
counting enable
source-zone Untrust
destination-zone Trust
destination-ip-host 172.16.10.100
service https
rule 2 name local2untrust
action pass
source-zone Local
rule 100 name t2ut
action pass
source-zone trust
destination-zone untrust
destination-zone local
destination-ip-host 172.16.10.1
destination-ip-subnet 172.16.20.0 255.255.255.0
#
五、删除安全策略规则rule 2
1、删除
#查找API手册可知,API为
DELETE /api/v1/SecurityPolicies/IPv4Rules?index=ID%3D1%3B
#新建DELETE请求,填入
https://10.88.142.143/api/v1/SecurityPolicies/IPv4Rules?index=ID%3D2%3B #Authorization选择API key,红框处填入“一、登陆防火墙”中获取到的token-id,然后点击send

#确认返回值为204
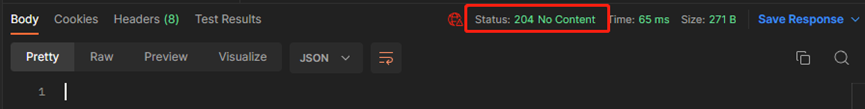
2、确认当前配置已经没有rule 2
#
security-policy ip
rule 0 name trust2untrust
action pass
logging enable
counting enable
source-zone Trust
destination-zone Untrust
source-ip-subnet 172.16.10.0 255.255.255.0
rule 1 name untrust2trust
action pass
counting enable
source-zone Untrust
destination-zone Trust
destination-ip-host 172.16.10.100
service https
rule 100 name t2ut
action pass
destination-zone untrust
destination-zone local
destination-ip-host 172.16.10.1
destination-ip-subnet 172.16.20.0 255.255.255.0
#
配置关键点
API参考官网手册即可,以F1000-AI防火墙为例,手册链接为:
https://www.h3c.com/cn/Service/Document_Software/Document_Center/Home/Security/00-Public/Developer_Guides/Development_Guide/H3C_SecPath_Comware_7_REST_API_Reference-7035/?CHID=788697
内容来源:知了社区,基于知识共享署名-相同方式共享3.0中国大陆许可协议CRM论坛(CRMbbs.com)——一个让用户更懂CRM的垂直性行业内容平台,CRM论坛致力于互联网、客户管理、销售管理、SCRM私域流量内容输出5年。 如果您有好的内容,欢迎向我们投稿,共建CRM多元化生态体系,创建CRM客户管理一体化生态解决方案。,使用Restful查看/新增/删除V7防火墙安全策略配置




