单畅,F1000防火墙用iNode拨L2tp over ipsec典型配置
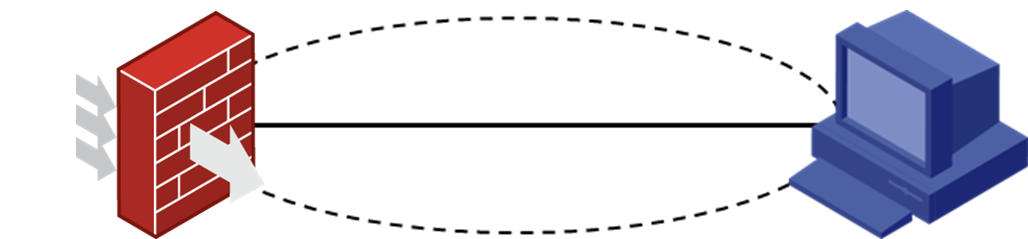
组网及说明
配置步骤
设备侧配置:
#
interface Virtual-Template1
ppp authentication-mode chap domain system
remote address pool 1
ip address 192.168.10.1 255.255.255.0
#
interface GigabitEthernet0/1
port link-mode route
combo enable copper
ip address 113.135.195.230 255.255.255.224
nat outbound
ipsec apply policy 1
#
interface GigabitEthernet0/2
port link-mode route
ip address 172.168.100.1 255.255.255.0
#
local-user vpn class network
password cipher $c$3$HQmQBQquyfz0iPV52E+t2OkKba7Vn9A=
service-type ppp
authorization-attribute user-role network-operator
#
ipsec transform-set 1
encapsulation-mode tunnel
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm md5
#
ipsec transform-set 2
encapsulation-mode tunnel
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm md5
#
ipsec transform-set 3
encapsulation-mode tunnel
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec transform-set 4
encapsulation-mode tunnel
esp encryption-algorithm aes-cbc-192
esp authentication-algorithm md5
#
ipsec transform-set 5
encapsulation-mode tunnel
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec transform-set 6
encapsulation-mode tunnel
esp encryption-algorithm aes-cbc-256
esp authentication-algorithm md5
#
ipsec policy-template 1 1
transform-set 1 2 3 4 5 6
local-address 113.135.xx.xx
ike-profile 1
reverse-route dynamic
#
ipsec policy 1 1 isakmp template 1
#
l2tp-group 1 mode lns
allow l2tp virtual-template 1
undo tunnel authentication
#
l2tp enable
#
ike profile 1
keychain 1
local-identity fqdn LNS
match remote identity address 0.0.0.0 0.0.0.0
match remote identity user-fqdn LAC
match remote identity fqdn LAC
proposal 1 2 3 4 5 6
#
ike profile q
#
ike proposal 1
encryption-algorithm aes-cbc-128
dh group2
authentication-algorithm md5
#
ike proposal 2
encryption-algorithm 3des-cbc
dh group2
authentication-algorithm md5
#
ike proposal 3
encryption-algorithm 3des-cbc
dh group2
#
ike proposal 4
encryption-algorithm aes-cbc-256
dh group2
#
ike proposal 5
dh group2
#
ike proposal 6
encryption-algorithm aes-cbc-192
dh group2
#
ike keychain 1
pre-shared-key address 0.0.0.0 0.0.0.0 key cipher $c$3$AY0t5qKEqCJlFOXDUAtStcB6ckWRN/0=
#
iNode上配置:
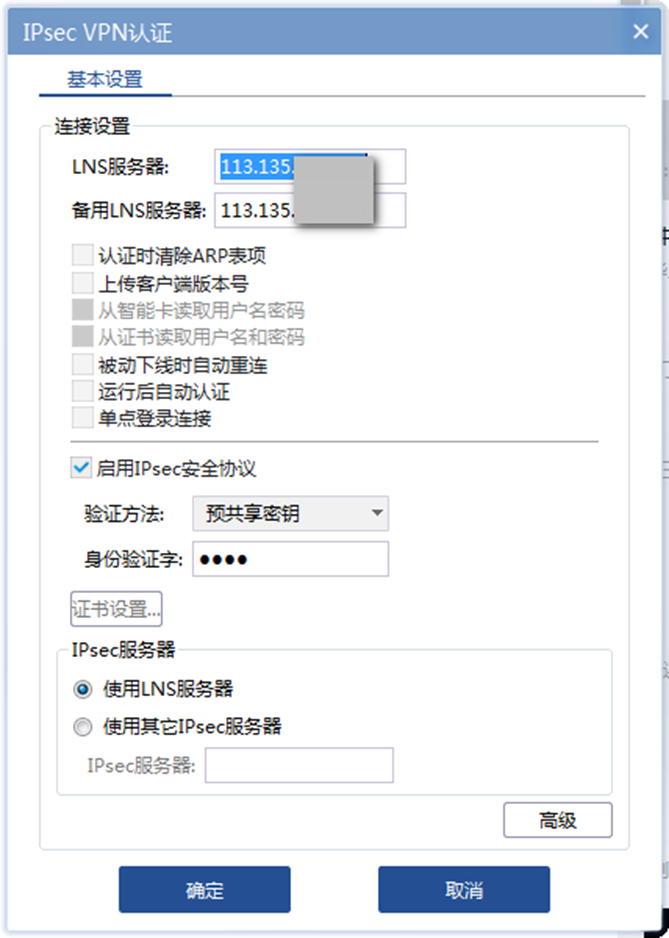
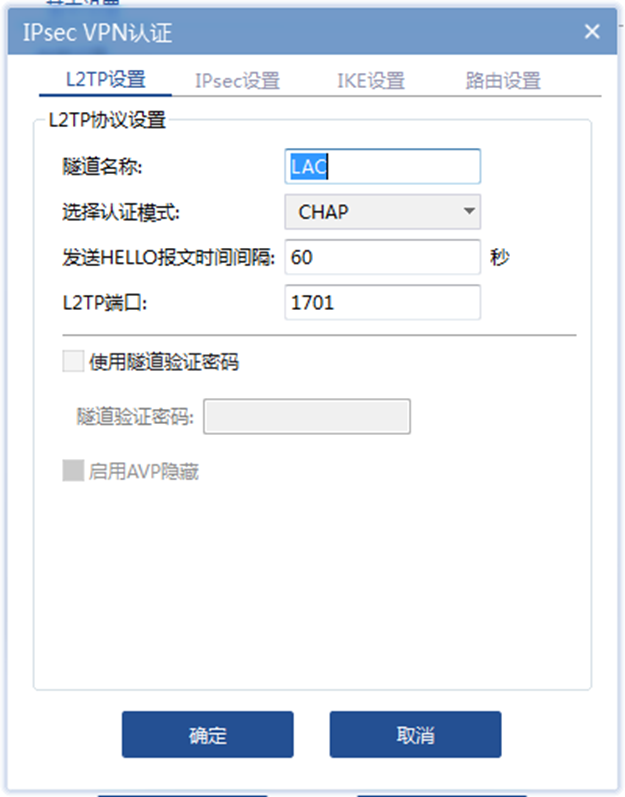
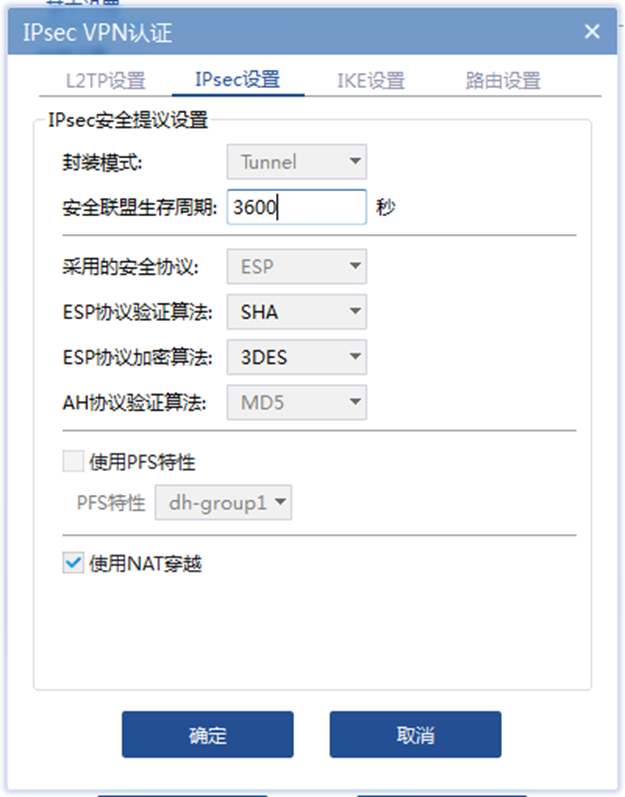
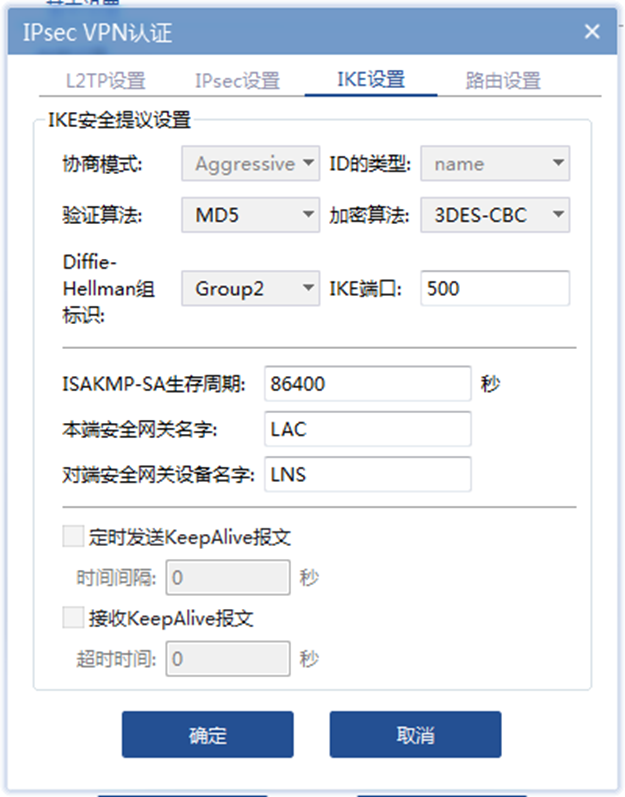
配置关键点
设备侧 ipsec配置需要注意:
1、两边的加密算法需保持一致;
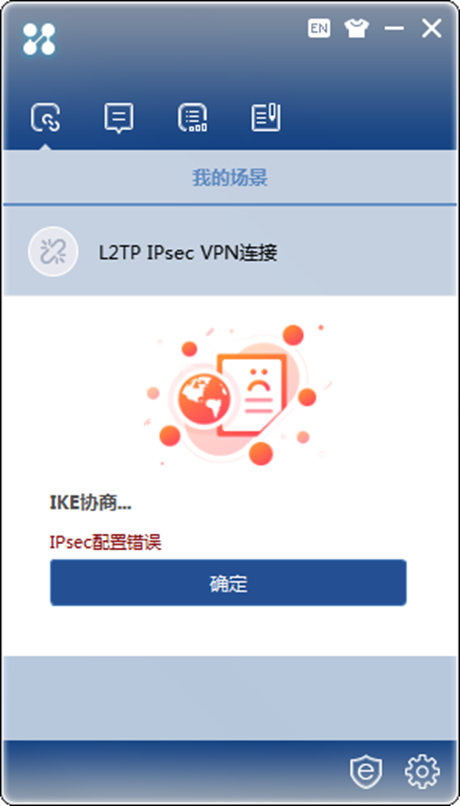
2、与iNode对接,ipsec transform-set 里 encapsulation-mode tunnel 安全提议需要配置为传输模式。否则会iNode侧拨号会建立失败,有如下报错: